Both ACTATEK and NITGEN offer highly advanced biometrics Facial Recognition and Finger Print Technology that surpasses its competitors. Hybrid models may offer a combination of Facial Recognition Technology + Smart Cards. Any combination is available throughout the offering for both brands. Choose the right technology for your purposes of time attendance management. Combination models can be hosted on the same server software platform. This is a boost where both biometrics and card systems can be used for different purposes in the proposed system.
BIOMETRICS THE WAY TO GO!

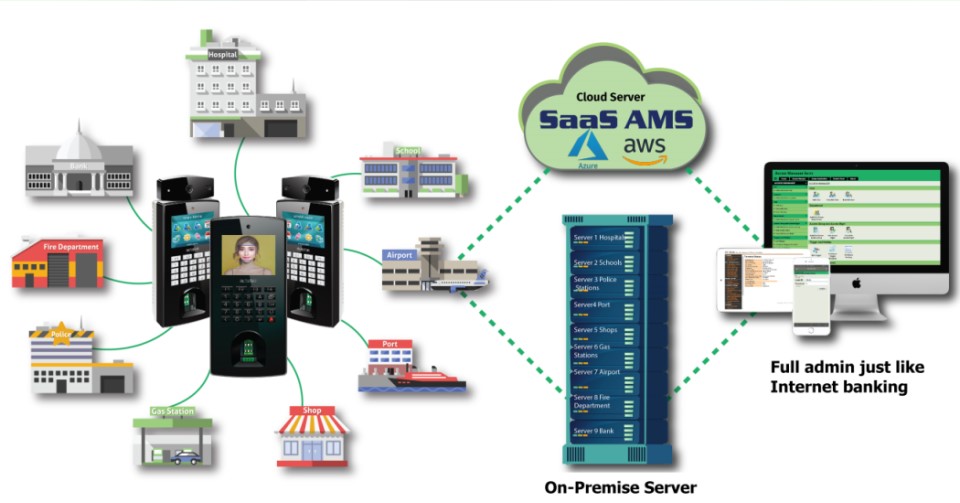
Why ACTAtek?
The leading Biometrics and card based systems offering web technology.
Best technology with a full featured server software ensures clients can manage the system with little intervention. The system is so reliable that thousands of actatek readers installed 12 years ago are still functioning till today. This a system hard to beat if you are considering for time attendance or door access management purposes. This system has been around for almost 2 decades and still the power house in its category.
Why NITGEN?
Nitgen is now the forefront of the Facial Recognition offering. The Ubio series is superior to almost any brand out there in the market. With such high end quality and features, the Ubio is priced affordably. With superior features and a robust database software its taking the market by storm.
There is nothing quite close to the Ubio series when it comes down to performance, accuracy and reliability. Clients are adopting the Ubio series once they observe the features and ease of use.
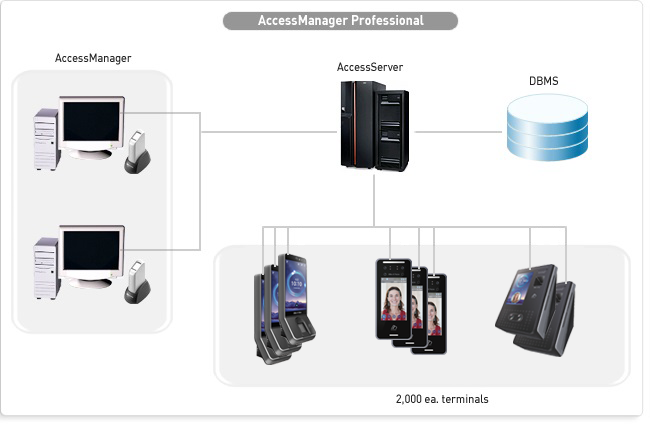
Quality comes with a Price. With Actatek and Nitgen, the features, reliability and ease of use outweighs the price offering. TMS ensures that clients receive systems that are value of money and in turn become good references.
The Differences between Readers for Time Attendance and Door Access Management
Time Attendance Readers
- They have activity based triggers where users can select: Work In, Work Out, Lunch In, Lunch Out, Overtime In, Overtime Out, Casual Time In, Casual Time Out
- They must be accurate and highly reliable
- They must offer 24/7 performance and designed for time attendance capture
- Clinic Visit
- Travelling for meetings from the office
- Company Car Key management
- Company Asset management
- Received Payment
- Attended Meeting
- Roll Call for Disaster Management in factories, offices, etc
- Up to 40 different triggers can be programmed
- Real Time Data of every transaction captured
- The Readers can work on standalone mode in the case of a network outage
- Internal buffering up to 10 Million transactions
- Auto upload of all buffered transactions to central server database
- Able to synchronize all Users details and settings across all readers
- Does not rely on “middleware” as every reader has a internal memory storage
- SSL Encrypted for anti-hacking
- Fully web based and full TCP/IP architecture
- Ability to roll back
- Time Attendance Readers are critical for time sheet preparation and hence payroll. Must be highly reliable and accurate.
Door Access Readers
- Most are slave readers connected to “middleware” such as controllers
- Multiple slave readers to 1 controller. When controller develops a hiccup all readers connected to the controller become “frozen”
- Door Access Readers are usually for door access. Therefore, multiple transactions for a User is captured for door log. Thus for time attendance purposes, the TA software has to filter logically the correct transaction to compute Work In and Work Out based on Last In and Last Out.
- If the User did not Log Out, the system might compute the Last Work In and the next days Work In as one full working day thus creating an error.
- Door Access is not critical for real time purposes. Only when a breach occurs, the admin person will access and study which User has breached the door access.
- Door Access Readers do not have Triggers. Only Access In and Access Out is recorded.
- The severity of the use of the door access reader is low as compared to a Time Attendance Reader where thousands of Users are authenticating every day on a minimum of at least 2-4 times daily.
- Most access readers are wired with RS232/485 and controllers with network. In terms of cabling costs and maintenance is far more difficult and not as cost efficient as the Readers with full TCP/IP technology.
